Difference between revisions of "UsingSSH"
| (47 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
'''Using SSH to connect to machines and to move data''' | '''Using SSH to connect to machines and to move data''' | ||
=Introduction= | =Introduction= | ||
| + | The goal for this page is to provide a 'how-to' guide for several topics related to using the Secure Shell--SSH. | ||
| − | =Using Key-Pairs= | + | =Using SSH Key-Pairs= |
==Creating the Keys== | ==Creating the Keys== | ||
| Line 16: | Line 17: | ||
<pre> | <pre> | ||
Generating public/private rsa key pair. | Generating public/private rsa key pair. | ||
| − | Enter file in which to save the key (/ | + | Enter file in which to save the key (/home/gethin/.ssh/id_rsa): |
</pre> | </pre> | ||
| − | The default filename suggested is fine, so accept it by hitting | + | The default filename suggested is fine, so accept it by hitting '''return'''. |
Next you are prompted for a '''passphrase''': | Next you are prompted for a '''passphrase''': | ||
| Line 26: | Line 27: | ||
</pre> | </pre> | ||
| − | Think of a strong, yet memorable one and enter it. (One tip is to think of a phrase, saying, song lyric etc. For example "One small step for man, one giant leap for mankind." Then take the first letters from each word, perhaps substituting digits for letters, to create the passphrase, "Oss4mogl4m.") You will be prompted for your passphrase twice: | + | Think of a strong, yet memorable one and enter it. (One tip is to think of a phrase, saying, song lyric etc. For example "'''One small step for man, one giant leap for mankind'''." Then take the first letters from each word, perhaps substituting digits for letters, to create the passphrase, "'''Oss4mogl4m'''.") You will be prompted for your passphrase twice: |
<pre> | <pre> | ||
| Line 35: | Line 36: | ||
<pre> | <pre> | ||
| − | Your identification has been saved in / | + | Your identification has been saved in /home/gethin/.ssh/id_rsa. |
| − | Your public key has been saved in / | + | Your public key has been saved in /home/gethin/.ssh/id_rsa.pub. |
The key fingerprint is: | The key fingerprint is: | ||
| − | 37:7a:b3:81:e2:0e:fa:5e:b2:df:84:a5:fb:f9:e6:f7 | + | 37:7a:b3:81:e2:0e:fa:5e:b2:df:84:a5:fb:f9:e6:f7 |
</pre> | </pre> | ||
| + | |||
| + | If you look inside the directory '''~/.ssh''' you will see two files: | ||
| + | * '''id_rsa''' is your '''private key''' | ||
| + | * '''id_rsa.pub''' is your '''public key''' | ||
==Distributing Your Public Key== | ==Distributing Your Public Key== | ||
| − | + | Now that you have your key-pair, you can copy your '''public key''' to any machine that you would like to connect to from the machine that you are currently logged into. When the keys are setup correctly, you will be able to '''connect without typing your password'''. Hurrah for the convenience! | |
| + | |||
| + | The first step is to ensure that the permissions on your files are correct. The following commands will take care of this: | ||
| + | |||
| + | <pre> | ||
| + | cd ~/.ssh | ||
| + | chmod 600 * | ||
| + | cd ~ | ||
| + | chmod 700 .ssh | ||
| + | </pre> | ||
| + | |||
| + | Now, let's copy your public key to the remote host of interest. In this case, I want to be able to login '''to''' a machine called '''brian''', '''from''' one called '''dylan''': | ||
| + | |||
| + | <pre> | ||
| + | scp ~/.ssh/id_rsa.pub brian:~/.ssh/from-host.pub | ||
| + | </pre> | ||
| + | |||
| + | (I'm assuming here that your username matches on the two machines. If not, you can prepend your username to the destination string, i.e. <username>@brian:~/.ssh/from-dylan.pub.) | ||
| + | |||
| + | Now, login to the remote host in the normal way: | ||
| + | |||
| + | <pre> | ||
| + | ssh brian | ||
| + | </pre> | ||
| + | |||
| + | where you will be prompted for your password, as per usual: | ||
| + | |||
| + | <pre> | ||
| + | gethin@brian's password: | ||
| + | </pre> | ||
| + | |||
| + | The following commands will: | ||
| + | |||
| + | # ensure that your file permissions are correct on the remote host | ||
| + | # add your public key to the list of authorized keys | ||
| + | # exit from the remote host | ||
| + | |||
| + | <pre> | ||
| + | chmod 700 ~/.ssh | ||
| + | cd ~/.ssh | ||
| + | chmod 600 * | ||
| + | cat from-host.pub >> authorized_keys | ||
| + | exit | ||
| + | </pre> | ||
| + | |||
| + | Now, when you connect to your remote host: | ||
| + | |||
| + | <pre> | ||
| + | ssh brian | ||
| + | </pre> | ||
| + | |||
| + | you will be prompted for your passphrase rather than your password: | ||
| + | |||
| + | <pre> | ||
| + | Enter passphrase for key '/home/gethin/.ssh/id_rsa': | ||
| + | </pre> | ||
| + | |||
| + | Some progress! you may say, and at first blush you are (almost) right, but hang on a moment and we will see how we can connect to remote hosts with keys set up this way, only having to type your passphrase once. | ||
| + | |||
| + | Since you're currently logged in to your remote host, we may as well do a little tidying: | ||
| + | |||
| + | <pre> | ||
| + | rm ~.ssh/from-host.pub | ||
| + | exit | ||
| + | </pre> | ||
==Using ssh-agent== | ==Using ssh-agent== | ||
| + | |||
| + | Enter '''ssh-agent''' and the potential for passwordless logins. | ||
| + | |||
| + | A quick way to try this out is to type: | ||
<pre> | <pre> | ||
| Line 51: | Line 124: | ||
</pre> | </pre> | ||
| − | ==Using ssh- | + | This will start a bash shell as the ''child'' of the ssh-agent process. (You may like to substitute '''bash''' with your shell of choice.) |
| + | |||
| + | Now type: | ||
| + | |||
| + | <pre> | ||
| + | ssh-add | ||
| + | </pre> | ||
| + | |||
| + | and you will be prompted for your passphrase: | ||
| + | |||
| + | <pre> | ||
| + | Enter passphrase for /home/gethin/.ssh/id_rsa: | ||
| + | </pre> | ||
| + | |||
| + | if you type correctly, you will get a confirmation: | ||
| + | |||
| + | <pre> | ||
| + | Identity added: /home/gethin/.ssh/id_rsa (/home/gethin/.ssh/id_rsa) | ||
| + | </pre> | ||
| + | |||
| + | and now when you connect to your remote host, '''you won't need to enter a thing!''' You can exit and connect again. Still no need for a password. You can start an xterm and connect from there. No password required. As you can see, '''all child processes can use the cached passphrase added to your agent'''. | ||
| + | <!-- | ||
| + | ===Automating the Agent=== | ||
| + | |||
| + | '''Note that the approach below will work for single ssh connections. Multiple invocations of this start-up procedure will not work as expected.''' | ||
| + | |||
| + | We can make the process of starting an agent and adding your keys more automated, and hence convenient than the steps above. First of all, create a file called '''~/.ssh/setup''' containing the following text: | ||
| + | |||
| + | <pre> | ||
| + | #!/bin/sh | ||
| + | |||
| + | # Checks for current ssh agent, otherwise starts one. | ||
| + | |||
| + | # For bash and ksh users: | ||
| + | # | ||
| + | # include the following in your ~/.bashrc or ~/.kshrc or ~/.profile | ||
| + | # | ||
| + | # . $HOME/.ssh/setup | ||
| + | # | ||
| + | # For csh and tcsh users: | ||
| + | # | ||
| + | # include the following in your ~/.cshrc or ~/.tcshrc | ||
| + | # | ||
| + | # source $HOME/.ssh/setup | ||
| + | # | ||
| + | |||
| + | SSH_ENV="$HOME/.ssh/environment" | ||
| + | |||
| + | function start_agent { | ||
| + | echo "Initialising new SSH agent..." | ||
| + | /usr/bin/ssh-agent | sed 's/^echo/#echo/' > "${SSH_ENV}" | ||
| + | echo succeeded | ||
| + | chmod 600 "${SSH_ENV}" | ||
| + | . "${SSH_ENV}" > /dev/null | ||
| + | /usr/bin/ssh-add; | ||
| + | } | ||
| + | |||
| + | # Source SSH settings, if applicable | ||
| + | |||
| + | if [ -f "${SSH_ENV}" ]; then | ||
| + | . "${SSH_ENV}" > /dev/null | ||
| + | ps -ef | grep ${SSH_AGENT_PID} | grep ssh-agent$ > /dev/null || { | ||
| + | start_agent; | ||
| + | } | ||
| + | else | ||
| + | start_agent; | ||
| + | fi | ||
| + | </pre> | ||
| + | |||
| + | ===For BASH=== | ||
| + | |||
| + | Add: | ||
| + | |||
| + | <pre> | ||
| + | . $HOME/.ssh/setup | ||
| + | </pre> | ||
| + | |||
| + | to your '''~/.bashrc''', and: | ||
| + | |||
| + | <pre> | ||
| + | kill $SSH_AGENT_PID | ||
| + | </pre> | ||
| + | |||
| + | to your '''~/.bash_logout''' | ||
| + | |||
| + | ===For KSH=== | ||
| + | |||
| + | <pre> | ||
| + | . $HOME/.ssh/setup | ||
| + | trap ". ~/.logout" EXIT | ||
| + | </pre> | ||
| + | |||
| + | to your '''.kshrc''', and: | ||
| + | |||
| + | <pre> | ||
| + | kill $SSH_AGENT_PID | ||
| + | </pre> | ||
| + | |||
| + | to your '''~/.logout''' | ||
| + | |||
| + | Now you will be prompted for your passphrase only once, at login and all other connections will be passwordless. | ||
| + | |||
| + | ===A Snag with SCP=== | ||
| + | |||
| + | With the above setup, you a prompted for any passphrases at login time. If you are attempting to run '''scp''' from a third machine, connecting to e.g. '''dylan''', it will hang due to the passphrase prompt. | ||
| + | |||
| + | To get around this, you will need to setup your keys to connect to dylan, prior to adding any automation to your .bashrc or .kshrc. | ||
| + | |||
| + | --> | ||
| + | |||
| + | ==Appendix: Cleaning Away Old Keys--If Required!== | ||
| + | |||
| + | If you need to remove some existing keys for any reason (for example you set them up without passphrases, and now you want to create more secure versions), here is the procedure that you should follow: | ||
| + | |||
| + | # login to the machine that holds your private key ('''dylan''' in the examples above) and remove the files '''.ssh/id_rsa''' and '''.ssh/id_rsa.pub'''. | ||
| + | # Next login to the ''destination'' host for your key pair, i.e. the machine which you copied your public key onto. ('''brian''' in the examples). | ||
| + | # open the file '''.ssh/authorized_keys''' (it's a text file) and '''delete the line''' corresponding to the machine that you would be connecting from, e.g.<pre>ssh-rsa AAAAB3NzaC1yc......== gethin@dylan</pre> | ||
| + | # Now you're in a position to create some new keys. | ||
| + | |||
| + | =Using SSH Config Files= | ||
| + | |||
| + | If you regularly connect to several remote machines, perhaps using different usernames, the file '''.ssh/config''' offers you some convenient shortcuts. You can store entries such as: | ||
| + | |||
| + | <pre> | ||
| + | Host newblue | ||
| + | HostName bluecrystalp3.acrc.bris.ac.uk | ||
| + | User gethin | ||
| + | </pre> | ||
| + | |||
| + | in your SSH config file. This will allow you to type '''ssh newblue''' to connect as: '''gethin@bluecrystalp3.acrc.bris.ac.uk'''. The use of such nicknames can save you considerable typing. | ||
| + | |||
| + | =Transparent Multi-hop SSH= | ||
| + | |||
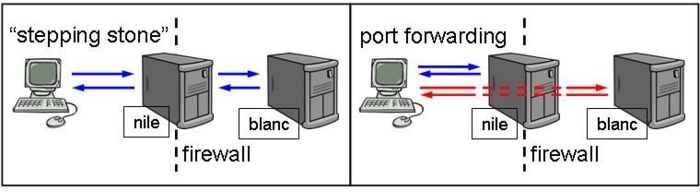
| + | [[Image:Port-forwarding.jpg|700px|thumbnail|center|Port forwarding with SSH]] | ||
| + | |||
| + | We would like to connect to blanc, but it is behind a firewall. One approach is to connect to each in turn, using '''nile''' as a '''stepping stone'''. Another approach is to setup a transparent multi-hop connection in your SSH config file so that you can seemingly connect directly, to '''blanc'''. Here's how: | ||
| + | |||
| + | <pre> | ||
| + | Host blanc | ||
| + | User blanc-user | ||
| + | HostName blanc.uni.ac.uk | ||
| + | ProxyCommand ssh nile-user@nile.uni.ac.uk nc %h %p 2> /dev/null | ||
| + | </pre> | ||
| + | |||
| + | Now we can simply copy a file directly from blanc onto our local machine using scp: | ||
| + | |||
| + | <pre> | ||
| + | scp blanc:path/to/remote/file path/to/local/file | ||
| + | </pre> | ||
| + | |||
| + | see also: http://sshmenu.sourceforge.net/articles/transparent-mulithop.html | ||
Latest revision as of 11:35, 15 November 2013
Using SSH to connect to machines and to move data
Introduction
The goal for this page is to provide a 'how-to' guide for several topics related to using the Secure Shell--SSH.
Using SSH Key-Pairs
Creating the Keys
First, let's create a key-pair. Start by typing:
ssh-keygen
You will see a message like:
Generating public/private rsa key pair. Enter file in which to save the key (/home/gethin/.ssh/id_rsa):
The default filename suggested is fine, so accept it by hitting return.
Next you are prompted for a passphrase:
Enter passphrase (empty for no passphrase):
Think of a strong, yet memorable one and enter it. (One tip is to think of a phrase, saying, song lyric etc. For example "One small step for man, one giant leap for mankind." Then take the first letters from each word, perhaps substituting digits for letters, to create the passphrase, "Oss4mogl4m.") You will be prompted for your passphrase twice:
Enter same passphrase again:
When the key-pair creation is completed, you will get some lines of text as confirmation, such as:
Your identification has been saved in /home/gethin/.ssh/id_rsa. Your public key has been saved in /home/gethin/.ssh/id_rsa.pub. The key fingerprint is: 37:7a:b3:81:e2:0e:fa:5e:b2:df:84:a5:fb:f9:e6:f7
If you look inside the directory ~/.ssh you will see two files:
- id_rsa is your private key
- id_rsa.pub is your public key
Distributing Your Public Key
Now that you have your key-pair, you can copy your public key to any machine that you would like to connect to from the machine that you are currently logged into. When the keys are setup correctly, you will be able to connect without typing your password. Hurrah for the convenience!
The first step is to ensure that the permissions on your files are correct. The following commands will take care of this:
cd ~/.ssh chmod 600 * cd ~ chmod 700 .ssh
Now, let's copy your public key to the remote host of interest. In this case, I want to be able to login to a machine called brian, from one called dylan:
scp ~/.ssh/id_rsa.pub brian:~/.ssh/from-host.pub
(I'm assuming here that your username matches on the two machines. If not, you can prepend your username to the destination string, i.e. <username>@brian:~/.ssh/from-dylan.pub.)
Now, login to the remote host in the normal way:
ssh brian
where you will be prompted for your password, as per usual:
gethin@brian's password:
The following commands will:
- ensure that your file permissions are correct on the remote host
- add your public key to the list of authorized keys
- exit from the remote host
chmod 700 ~/.ssh cd ~/.ssh chmod 600 * cat from-host.pub >> authorized_keys exit
Now, when you connect to your remote host:
ssh brian
you will be prompted for your passphrase rather than your password:
Enter passphrase for key '/home/gethin/.ssh/id_rsa':
Some progress! you may say, and at first blush you are (almost) right, but hang on a moment and we will see how we can connect to remote hosts with keys set up this way, only having to type your passphrase once.
Since you're currently logged in to your remote host, we may as well do a little tidying:
rm ~.ssh/from-host.pub exit
Using ssh-agent
Enter ssh-agent and the potential for passwordless logins.
A quick way to try this out is to type:
ssh-agent bash
This will start a bash shell as the child of the ssh-agent process. (You may like to substitute bash with your shell of choice.)
Now type:
ssh-add
and you will be prompted for your passphrase:
Enter passphrase for /home/gethin/.ssh/id_rsa:
if you type correctly, you will get a confirmation:
Identity added: /home/gethin/.ssh/id_rsa (/home/gethin/.ssh/id_rsa)
and now when you connect to your remote host, you won't need to enter a thing! You can exit and connect again. Still no need for a password. You can start an xterm and connect from there. No password required. As you can see, all child processes can use the cached passphrase added to your agent.
Appendix: Cleaning Away Old Keys--If Required!
If you need to remove some existing keys for any reason (for example you set them up without passphrases, and now you want to create more secure versions), here is the procedure that you should follow:
- login to the machine that holds your private key (dylan in the examples above) and remove the files .ssh/id_rsa and .ssh/id_rsa.pub.
- Next login to the destination host for your key pair, i.e. the machine which you copied your public key onto. (brian in the examples).
- open the file .ssh/authorized_keys (it's a text file) and delete the line corresponding to the machine that you would be connecting from, e.g.
ssh-rsa AAAAB3NzaC1yc......== gethin@dylan
- Now you're in a position to create some new keys.
Using SSH Config Files
If you regularly connect to several remote machines, perhaps using different usernames, the file .ssh/config offers you some convenient shortcuts. You can store entries such as:
Host newblue HostName bluecrystalp3.acrc.bris.ac.uk User gethin
in your SSH config file. This will allow you to type ssh newblue to connect as: gethin@bluecrystalp3.acrc.bris.ac.uk. The use of such nicknames can save you considerable typing.
Transparent Multi-hop SSH
We would like to connect to blanc, but it is behind a firewall. One approach is to connect to each in turn, using nile as a stepping stone. Another approach is to setup a transparent multi-hop connection in your SSH config file so that you can seemingly connect directly, to blanc. Here's how:
Host blanc User blanc-user HostName blanc.uni.ac.uk ProxyCommand ssh nile-user@nile.uni.ac.uk nc %h %p 2> /dev/null
Now we can simply copy a file directly from blanc onto our local machine using scp:
scp blanc:path/to/remote/file path/to/local/file
see also: http://sshmenu.sourceforge.net/articles/transparent-mulithop.html